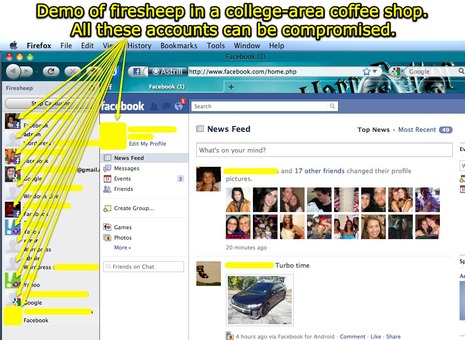
Firesheep cometh; is open WiFi safe anymore?
Given how many active cruisers rely on WiFi, the advent of Firesheep — which apparently makes it super easy to break into people’s web accounts when they are on the same WiFi network — deserves more than my comment on the Rogue Wave entry. I first heard about the problem via a dire-sounding ActiveCaptain newsletter, and I’ve since corresponded with Jeff Siegle who says boaters need to be warned. To get an idea of how dangerous Firesheep and copycat programs are, Jeff tried one while anchored off a marina and reports that he “got passwords from half the boats with people aboard – all
without them knowing.” This tech blog, home of the illustration above, is also pretty dire, but, like so many internet security issues, this one seems somewhat confusing…
For instance, while Jeff thinks it’s important for marinas to encrypt their open WiFi, Richard — the tech whiz at Wave WiFi — says this new problem applies to any AP “including a marina using encryption.” Some sources seem to say that the dangers lie mostly with social sites like Facebook, others say it’s more pervasive. And of course lots of tech sites have suggestions about what we should do, like TechCrunch, and Technologizer. Is there a significant problem, should cruisers avoid open WiFi networks as much as possible, or what?
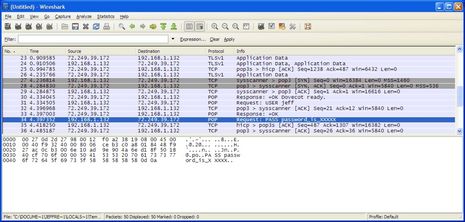
PS I asked Jeff for an illustration of his sniffer testing and while he decided grabbing real passwords was a “bad idea” he did demo the process on his own email server, illustration below. Note that the POP email account is faked and the password failed. Jeff used Wireshark, which he says is not for the “average person” but he goes to say that “What’s happening now is that
tools like Firesheep are making it much more user-friendly to grab this
type of information and exploit it. THAT’S the big change.”
Jeff’s explanation of what’s happening on this screen: “sysscanner > pop3” is a computer on the network asking to speak to ActiveCaptain’s email server; “Response: +OK Dovecot ready” is ActiveCaptain saying, go ahead; “Request: USER jeff” is the computer asking for the account name “jeff” (as in [email protected]); “pop3 > sysscanner” is an acknowledgement that the packet was received; “Response: +OK” is ActiveCaptain saying the the account is OK; “Request: PASS password_is_XXXXX” is the computer sending the password
for “jeff” in the open – I actually entered “password_is_XXXXX” for the
account. In this case, the server responded that the password is no good because,
well, I’m not giving out my password…
Grabbing other things like cookies, forms being typed on a web site, and
a whole host of other things is just as easy.









The software in question actually will work whether or NOT the AP is encrypted. It is sniffing packets thru the network, not listening over the wifi for packets. WPA offers no protections. Only https sites are safe!
Bill Lentz
Ben, a little more info here.
http://lifehacker.com/5672313/sniff-out-user-credentials-at-wi+fi-hotspots-with-firesheep
Bottom line for Wifi for us is VPN.
So if I never use Facebook or Twitter on the “Boat” computer and delete all cookies does this reduce my risk?
To be honest I have no interest in Twitter – just don’t understand the concept of why anyone would want to know every detail of my relatively boring day. Facebook is way to much personal information thrown out to the public than I want to release. Sounds like Firesheep is farming for social networks. Is there a possibility someone might be developing software to counter the hackers?
While WPA is not perfect, it surely provides protection from many of these types of attacks. I’m not sure I understand why Bill doesn’t think so when source after source, blog after blog gives the suggestion to use it. Again, I know it’s not perfect and other software can be used for DNS spoofing/ARP poisoning and probably other techniques to get around it. But for now, the average 14 year old in the condo next to the marina can’t use those techniques. For now.
References mentioning WPA as a fix:
http://steve.grc.com/2010/10/28/why-firesheeps-time-has-come/
http://www.zdnet.com/blog/networking/firesheep/278
http://urbanwireless.info/latest-news/377
http://open.salon.com/blog/authorfreeman/2010/11/07/firesheep_faq
There are hundreds of sites posting the same type of suggestion about WPA/WPA2 security. I really believe that marinas should enable WPA or WPA2 immediately.
Using a VPN is another solution. Unfortunately, this can have the effect of just shifting the trust to a company that is not very well known. I’ve been doing research into VPN providers and I’m shocked by how many don’t give much information about their organization…and how many end up being hosted in other countries across the world and sometimes in not-so-friendly locations.
It should be noted that cellular connectivity (aircards, MiFi – with default WPA, and tethered phones) don’t have these issues and are currently immune from these security attacks.
The VPN I mention above does not come from an outside provider. I own the server.
I agree with what Jeffrey says above. Just look at what Steve Gibson said (very well known computer security expert) in his post (as also mentioned by Jeffrey) at http://steve.grc.com/2010/10/28/why-firesheeps-time-has-come/
Steve lays it out in plain English, and the guy knows what he is talking about. WPA encryption for wireless routers is the best and easiest thing to do immediately. Then we wait for all of the sites that matter to go to FULL TIME HTTPS (you have to have a secure connection during the entire time you are connected to the website or else your account info is transmitted in the clear).
Listen to the following episode of Security Now (October 27th, episode 272) where Steve Gibson explains what is going on with Firesheep and what needs to be done. http://twit.tv/sn272
Bottom line is be smart when you are using a wireless connection. If it isn’t asking for a password, then you have no security what so ever from Firesheep.
Chris – you’re right. But that type of protection is outside the realm of most boaters especially if you’re doing extended cruising.
Also, is it quite rare for normal people to have their own server hardware in their possession. Having a rackspace type of provider where you’re essentially leasing a server requires a much better security agreement than most GoDaddy’s provide.
Until Facebook, twitter, and other companies sort out their end to end encryption, VPN or SSHtunnel is only truely secure options when using public wifi. :-/
However, for those yachtie types who are a bit low tech: you can try Blacksheep. It will at least tell you if someone is using FireSheep.
http://research.zscaler.com/2010/11/blacksheep-tool-to-detect-firesheep.html
TIM
Let’s be honest, open WiFi hasn’t been safe since 802.11 was originally written in 1997.
What’s changed is publicity. It used to be that anyone who knew a bit about how network connections work, and could write simple scripts, could install the appropriate tools and sniff your data off the open WiFi. Now, you don’t even need the technical knowledge- any prankster with a mouse and keyboard can install a browser extension and snoop around.
The other new thing is the social networks. They don’t care one iota about security. Any site that stores your session data as a plain text HTTP cookie is screaming “come in and mess around!”.
What needs to happen is for “Joe Average User” to realize that, hey, anything I type can and will be watched and exploited unless I do something about it.
I’m hoping that Firesheep, Blacksheep, etc. will help make people more aware of these issues. But I’m not holding out hope- I still get a lot of quizzical “WTF is this?” when people see the PGP signature on my emails, and not many seem to know what the “s” in “https” means and why it’s needed.
Jeff et.al. can you comment on using smart phones on free wifi? What are the dangers of using my iPhone on the coffee shop’s wifi?
Just a couple of comments as things are getting a bit jumbled in this thread I think.
The test that Ben and Jeff ran doesn’t really have anything to do with Firesheep. The issue with your example/demo is you are downloading your email from an unsecured server (as best as I can tell from what was written and the screen shot). Its just like going to a banking site without HTTPS, you should never do this. You should not be using unsecured POP/IMAP servers because of what you have shown. Anyone watching the “traffic” can see anything that is not encoded with SSL (HTTPS), including user id’s and passwords, as well as the contents of all your email.
So, for your test, this is nothing new as any non secured transmission (non-https) can be watched without too much effort, independent of the encryption of the wireless. The owner of the router can see every bit of data going in and out if you are not accessing an HTTPS/SSL server, its that simple. It has nothing to do with WiFi or the encryption that is enabled (even WPA). You should get information from your email provider on how to set up your email client to access there server using SSL/TLS.
WEP/WPA/WPA2 only encrypts the wireless communication between you and the router. Anyone with access to the router can still view and see all of the data you are transmitting. So, securing the network will provide a little level of comfort as the number of people that can watch the traffic is decreased, but unless you know the owner, anyone with a computer wired to the router can still see everything anyway, again, this is nothing new.
As far as Firesheep, the best I can tell its not getting passwords for accounts (typically nothing can do this as the login pages are indeed HTTPS). It allows a hacker to hijack your session information and in turn, use your account (and as stated, this concept has been around a long time, Firesheep just made it trivial). Still a bad thing, yes, but it does not get the hacker access to your passwords. It does allow them to use your account for as long as the session is valid and post messages, and whatever else the website you are interacting with might let you do (again, will not work for full-HTTPS sites, like your bank).
So, yes, there are issues that need to get sorted out, especially if you use Facebook and other social networks, but stealing passwords is not really what this is about.
Just wanted to be clear about the example that was given, and the vulnerability of people with Firesheep.
Thanks, Mark, but for further clarification I didn’t do any sniff testing myself. Jeff used WireShark but his point is that “tools like Firesheep are making it much more user-friendly to grab this type of information and exploit it. THAT’S the big change.”
I think you’re right that Firesheep can’t sniff out passwords directly, but once a Firesheep user has hijacked your purportedly protected session at Facebook or Hotmail or etc., they can conceivably change your password or use your email account to have “forgotten” passwords sent to them.
Doug – there’s nothing special about the iPhone with regard to internet access. It is just as vulnerable. Note that Settings/General/Network has VPN controls built in so the means to a solution are there.
Mark – the example wasn’t to show how people are getting open passwords. It was meant to show how simple the data is to get. Tools like Firesheep take these network analyzers to the next level and make it all user-friendly so my mother can grab POP passwords. From first hand experience, there are plenty of POP passwords flying through the busy anchorages – I’ve looked.
Turning on WPA at a marina won’t eliminate the theoretical potential for data to be sniffed. But it does eliminate the practical potential. The major risk isn’t someone physically accessing the router. The risk is someone purposely and remotely sniffing data for illicit purposes. Turning on WPA will remove 99.9% of the issue which is good enough for most people.
Ben – Hotmail should be using HTTPS everywhere, so not a problem. This hijacking of session information will only work with sites that don’t use SSL for their ongoing interactions (as was pointed out).
So, assuming the hacker can’t get into your email account (which, if your using SSL they won’t), they wont be able to use the forgotten password feature of most sites. And to change a password directly, most reputable sites require you to type in your existing password prior to picking a new one, which will be impossible as well as the hacker does not know the passwords.
Again, passwords are not really the issue, if people secure their email. My guess is most people don’t know they can do this and hopefully now a few more do.
Jeff – No doubt that a secure wireless channel will help. But, people should know (and if they didn’t before, they do now), they should not be accessing email through unsecured servers. This data has always been readily available to anyone that really wanted to get it, including userid and password.
I agree that a secured wireless channel will help, but if you are accessing a “linksys” AP from your boat, I don’t agree you have eliminated 99.9% of your risk. I also was trying to educate people that this issue does not have to wholly with WiFi, as was being presented. Its the same thing Bill and Matt were trying to point out.
I am not trying to argue, or state that things were misrepresented, they were not. I simply thought the thread was a bit misleading for someone who is less than intimate with this stuff. They see a demo of getting passwords, and the thread is mostly about Firesheep, I would naturally relate the two, even though the two are unrelated.
The real morale of the story is work with secured servers (HHTPS/SSL/TLS) or be careful what you are doing anytime you are on a network you don’t own, which is basically 99% of the time for boaters. Such is life in the digital world. But, I personally would not sweat things too much as my important data, like username/pwd and CC/Banking info is all secured and not available to any of these tools. But others may have lower risk levels with WiFi (I don’t care if someone knows what books I am shopping for on Amazon for instance), just like with everything in life.
I forgot to mention one other thing also.
The security risk is not just at the access point you connect to (as I may have implied incorrectly). The data from that access point, to where ever its going (Amazon for instance), and back again, is all unsecured, with many, many, many (lots of many’s) devices and potentials for people to be watching the traffic.
Even when using a secured wireless connection, as soon as the data is traveling over the information superhighway, its susceptible for people to get the data, read the data, and use the data in a harmful manner.
That is why others have stated securing a wireless connection is not really the solution. It might help some, but if a bad guy wants your data, securing the WiFi connection isn’t really going to help that much. This is my opinion of course, and I am sure some people will put a bigger weight on the WiFi connection itself as the main security issue.
But Mark, come on. You’re a manufacturer of WiFi equipment for boats. You know a significant more about all of these issues than every other cruiser out there. You know when you’re protected and what activities are dangerous. Most cruisers out there have no idea and can’t begin to understand the nuances of network protocols and the alphabet soup of acronyms like SSL/TLS/ARP/DNS/etc.
I believe the only responsible thing to do is provide a clear message to all cruisers right now: Don’t use open WiFi.
Anything else is just creating noise and confusion in my opinion.
If I were a WiFi product manufacturer, I would surely want to make sure that all of my customers were protected. Let a few more stories come out about accounts being compromised (like I’ve been told about the Krogen Cruiser’s list server) and you’ll find every cruiser dropping the use of WiFi from their boat – which I think would be a terrible thing.
I’m a retired security professional and do try this yourself at home and on the road.
Good (affordable) security comes from layers and disicpline. You want to thwart the greedy and lazy petty thief — if a pro or a government is after you, you need to hire a consultant. The mantra is basically: Protect the port, protect the channel, protect the handshake, protect the content, protect the protections and don’t be lazy. I have avoided jargon as much as possible.
PROTECT THE PORT — Don’t use public machines for anything identifiable to you. Expect them to have been compromised. When using your own machine, sit with your back to a wall, be aware of who is around you. Have a good firewall and malware suite loaded and in use — get one that stops traffic when it encounters a dubious security situation and requires you to explicitly allow the transaction to continue. Do not leave the machine unattended, ever, ever. Password protect the computer and set the sleep/lockdown time to as short as you can stand.
PROTECT THE CHANNEL — Use WPA where available and pick your spots for that availability — but realize a poorly managed WPA environment may provide false comfort, WPA keys/passwords can be comprimised by rank amateurs in less than 100 hours. Pick a spot that changes WPA keys/passwords daily if possible (very rare). If they don’t, assume you are running wide open. If you can, use a VPN. While VPN services’s credentials are hard to find, so is evidence anyone has been compromised by a well known, well advertised service. Use tethering from a cell phone for the small slice of content you really need to protect if a VPN isn’t the answer. Use smartphone banking/etc. apps if they work where you are.
PROTECT THE HANDSHAKE — Use “https://” for anything you can’t afford to lose. Even the encryption used by https will foil the intrusive amateur. Make sure the address bar of your browser highlights the connection type with color or a pop up. Many services will shift you seamlessly to http if https traffic bogs down. If you lose https when you need it, shut off the transaction immediately. At least one blogging service does this. If you can set your browser to “log off when https connection is lost,” do so.
PROTECT THE CONTENT — Obviously, for transactions with banks etc, you are stuck with their security framework — use every protection they offer/recommend, your ability to recover lost assets may depend on proving you did. For emails and such, if you don’t want people to see it, encrypt it. Use 256AES if you can and put the content that matters in an encrypted attachment. the best encrytion app is the one your correspondents will use. If your email service strips attachments, get a service that offers email encryption or learn to use an email text encrypter (although your correspondents may not care to). When sending encrypted content to an infrequent correspondent, use a self-extracting encryption app (it will create an encrypted file “yourcontent.exe”) and send the password via SMS or SMS to email. An “end-around” we have used for friends and family with limited computer tolerance is to post what would be email content to a blog via a service using https, password protect the post, and send them the permalink to the post (they already have the password).
PROTECT THE PROTECTIONS — Lock up your computer when it’s not being used (with physical access, I can crack a laptop with a reasonable 8 char password in about 10 minutes — the software to do this can be downloaded from multiple sources.) Password protect your computer. Password protect your passwords, put them in password “vault” protected by a master password and a key. Keep the key on several thumbdrives. Require both the master pw and key to access the passwords. Create serious passwords of 12-16 or more (is better) characters of near random content.* If you insist on saving passwords in the browser, put a serious master password on that browser. So far, I don’t know of any browser that effectively integrates security keys without a browser “extension” from essentially uncredentialed providers. Do not trust browser extensions that provide “improved security.”
*Writing down a master password is not a bad idea if you do so in away that requires you to solve a personal puzzle in the process. We have a nav chart with a series of fixes plotted that….
Jeff,
Not sure I understand what you mean. What I was trying to do was to offer some of my knowledge on this board as it all seemed a bit confusing, but maybe it was just me. Certainly you’re not implying I should be responsible for securing everyone’s network who buy’s our product, I don’t even think Cisco is up to that challenge.
My point is there is a lot more to it then just “Stop using open WiFi”.
You are leading people to believe that if they stop using Open WiFi they are more secure. I would simply argue that they are negligibly more secure, and does that warrant removing unsecured networks from one of the tools boaters have available to them? I don’t think so.
I think the thread on Crusiser’s forum should be quite a good read in the coming days.
http://www.cruisersforum.com/forums/f13/firesheep-wifi-security-issue-50250.html
While I fully appreciate Jeffs conerns and concur with most of it, the fact is that the technology to break an encryption within seconds on wi-fi has been around for a long time, the difference here only seems to be that it is being put “up-front” spectacularly in the public domain. Any serious hacker, identity theif or fraudster will already have the ability to do it.
It is down to the user to protect themselves, by not using credit card details etc on a wi-fi link public, home, or otherwise. Hackers are extremely unlikely to be interested in the normal day to day stuff of dowloading grib files, sending e.mails, etc from a boat. I can understand why Jeff is upset being that he Runs AC from his boat a lot of the time and there will probably be confidential info there, but the image of an army of hackers following Active Captain about is an unlikely one unless it is deliberate industrial espionage!!.
As Jeff says the answer is simple use a 3G connect for anything sensitive, although it is not true that a UMTS network cannot be hacked…it can,and GPRS/EDGE more easily, but does take some serious effort well outside the “Schoolboy” experience.
Ive learnt that over the years it doesnt matter what programs you write, or what encryption algorithms you use, someone will crack it, usually just for the challenge of doing it, but of course governments also have whole teams of people dedicated to this task too.
It’s just a reflection of the modern world I’m afraid that Big Brother (and little brother) is watching you, so take care out there!!
Steve
Stop using open WiFi? Use 3G?
C’mon guys, we’re not talking about the corporate office, we’re talking about recreational boaters cruising to new marinas and using marina or local hotspots. Like anything, we have to weigh pros and cons, and public WiFi is both Available (might be the only way to get online) and cheap (usually free or very inexpensive). Sure, I’d love to sell you a TracPhone or CruiseNet, but that’s out of the range of most boaters.
It’s important to know about these security holes and simply adjust our behavior so that we minimize risk. And tell the webmasters to implement SSL connections!
Well said Aaron, while I use a Fleet 150 Skipper unit, CruiseNet on Sprint, Kyocera KR-1 on VZW, an Ericsson W35 on AT&T and a high power Wave WiFi bridge router with a low power built in AP and install all of the above. WiFi is what it is. When I can I almost always chose WiFi when in a marina or at anchor. If your the type of cruiser that is worried about the government you wouldn’t be posting here in this thread anyway. I disable the WiFi on the various cellular modems and run them through a QOS LAN switch. The Fleet unit is only used by a direct LAN connection. I can rebroadcast the QOS LAN switch by rebroadcasting on my boat’s internal 5GHz 802.11A & N AP. I can also enable the cellular modems 802.11B & G AP’s as needed. I try and minimize the number of 2.4GHz B & G AP’s because of the limited number of channels we have and because I want peak performance from my Wave WiFi unit.
I haven’t seen anyone mention Bluetooth device ad hoc network security yet.
I’m not going to repeat all the above mentioned common sense protections you can take. Please remember the over the air 802.11 is just one layer of many in your path to the internet.
Maybe many on here are unaware that GSM has been hacked as well. If someone is that worried about interception then don’t use free Hot Spots it will be more available bandwidth for those of us that use, enjoy and install them.
We should be talking about the new FCC rulings on TV White Spaces WiFi instead of theft of service issues.
Bill Lentz
“disable the WiFi on the various cellular modems and run them through a QOS LAN switch. The Fleet unit is only used by a direct LAN connection. I can rebroadcast the QOS LAN switch by rebroadcasting on my boat’s internal 5GHz 802.11A & N AP. I can also enable the cellular modems 802.11B & G AP’s as needed. I try and minimize the number of 2.4GHz B & G AP’s ”
….
The point is, there are many many cruisers who read the above as total gobbletygook and have no idea what the eff any of that means. They are using old POP3 email accounts and 5 year old passwords on unsecure open WiFi connections and they don’t realize that my grandmother with Firesheep can see where they are logged in. And, until recently, it wasn’t really that easy. I think Jeff feels that Firesheep is a game changer in that way. Not everyone has to agree on that, but at least the word is getting around.
One more comment run a good firewall and have your computers with the latest security upgrades for your browser. Using HTTPS sites can’t be emphasized enough.
Bill Lentz
Ok Anonymous the “gobbletygook” and “eff” comments you talk about are sound advice. I would give cruisers more credit than you are. It’s also highly illegal to use programs like Firesheep for theft of people’s identities. Recently a server in China downloaded data from our US government so I guess you advocate people not use the internet at all?
You humor me Anonymous”.
Bill Lentz
Give this some thought why wouldn’t this work on users on the same cable system node? If you are running a laptop or data enabled device without security and not using HTTPS sites wouldn’t the same principles apply?
Bill Lentz
Ok, so just to put this in perspective. The attack is possible because other users are able to see your data in the first place.
WiFi unencrypted data can be captured by anyone, that’s a given.
With WPA, each device accessing a wireless network establishes it’s very own keys for data encryption. These keys are independent of pre-shared-secret (PSK), (i.e. a “password”) that is used to access the network. Once these keys are established, no 3rd party can readily snoop on communication between your device and the access point (leaving aside a possibility of cracking of an encryption protocol).
So, WPA does provide a pretty definitive protection against this type of attack and traditional password sniffers etc.
I use HotSpotShield for an easy to use and free VPN solution
http://www.hotspotshield.com/
Derek
HotSpot Shield may seem be free, but you pay for it with ads. Witopia Personal VPN (www.witopia.net) costs 40 bucks a year and gives you multiple, fast servers, extremely good suport, and it is supported for all popular platforms, including your iPhone and Android phone.
It is actually cheap, relative to its competition, and seems to be run by very clueful people.
Best,
Steve
Fantastic thread! I learned a lot about WiFi security but thank goodness for Wikipedia and the ability to look up all the acronyms, technical terms and how the wireless stuff developed. It all starts to become understandable to an old cruising end user like me. Thanks all.
What’s really unfortunate is that, as far as I can tell, only Mark Kilty above has a good grasp on what’s really going on. His remarks are the only ones that are both correct and not misleading.
That is unfortunate because understanding this type of technology (WiFi, encryption, routers) is the only way Internet communication can be made secure.
(Sorry if this sounds harsh; I don’t mean to offend anyone.)
Pandora wrote:
His remarks are the only ones that are both correct and not misleading.
Unfortunately, by making that statement with absolutely no credentials, it’s hard to tell whether your on the 802.11 standards committee with intimate knowledge of the issues….or are Mark’s mom.
No one disputes that WiFi security issues have existed since the word WiFi existed. But there’s something new that just changed and a lot of people think it changes everything. If you want to learn more, go see what the networking industry experts are suggesting – people like Steve Gibson. Have you actually read his posting on this exact subject? It’s still his main posting at:
http://steve.grc.com/
Just because you want to see open, public WiFi continue for who-knows-what reason, doesn’t mean it’s safe for the majority of boaters who don’t understand what most of the security issues are all about.
Thank you Jeff, that really helped sum it up for me why the issue is new and important, vs. the general knowledge that wifi is unsecure (without vpn)
But that’s just the problem Polarnavy, the algorithms and S/W are already out there in the criminal/corporate security/Gov world to crack the encryption.
But that’s taking it to a whole other level, which you’re average kid hacker won’t have access to, unless his Dad owns a security company.
There is an Israeli company who specialise in TV encryption who will design you your own “unhackable” system for a price, but of course that would need to be on both ends, which with wi-fi as it is isn’t possible.
Anyway maybe we’re just taking this a little too far, we’ve all known for a long time that it isn’t safe, and no form of internet communication is
entirely safe anyway. There’s always some new tool or other just around the corner. Just accept it for what it is and make your own risk assessment.
Otherwise let’s all go back to written mail or telegrams, or that old thing called the telephone and maybe the world would be a better and calmer place. I’m sort of in the middle here, whilst I fully appreciate Jeff’s concerns and agree with a lot of it, there comes a point where the technical effort required to keep ahead of the hacking game becomes self defeating in terms of the dynamics required. I suppose one solution would be for some company to take on the task of a sort of
wi-fi antivirus/mal-spy-hack ware, which would detect network intrusions and threats on the wi-fi RF signal and protocol layer itself. There may already be such a tool, but it’s always going to be playing catch up, just like PC protection is.
It’s Firesheep this month, maybe “Smokin’Goat” the month after and “Holy Cow” after that.
C’est lá vie.
Steve
We were planning to use “Smolderin’ Goat” now we have to have another focus group….
My software team suggested a solution to me that would protect our company laptops. It would appear this can apply to boaters as well.
“Using a VPN would actually make any Internet access private (up to the tunnel endpoint), even over public WiFi – no cooperation is required on the part of websites or wi-fi provider – assuming the usual case where the VPN client (installed on your computer) forces all traffic through the tunnel.
Some people, lacking access to a corporate VPN, choose to use public VPNs (aka anonymizing VPNs, of which there are plenty), while on a public WiFi.
The use of the VPN can be enforced on individual computers, like employee laptops, by disabling any network access, other than through the VPN tunnel.”
VPN’s are great solutions. Of course, it all depends on the VPN. All of your traffic will be completely in the open at the VPN site so you have to have a certain amount of trust in the VPN. How do you know if you can trust the VPN?
I’ve been making lists of providers – currently about 110 different ones. Some are free but insert advertising and often throttle your bandwidth. Others are located in countries that might not be considered friendly or secure. Many give you very little information about their credentials, reliability, or track record.
I made a requirements list of things a VPN provider should provide. It’s not obvious. Like for example, there’s a huge advantage if they have their servers spread out across the country and world and allow the ability to quickly switch between servers. This would allow you to watch streaming BBC TV because you could use a UK server that the BBC wouldn’t block. Or switch to another city to pick up an NFL game that is being blocked in your home area. There are also some technologies that VPN’s use that get blocked themselves by certain countries including parts of Canada. Options to get around that have to be trivial.
I have a short list of a few providers that I like and who meet the dozen requirements. I’ve been interviewing them to make some direct contact and learn more. Gut feel is important too. I hope to provide a recommendation in the next couple of weeks of a provider that would work well for cruising boaters.
“Otherwise let’s all go back to written mail or telegrams, or that old thing called the telephone and maybe the world would be a better and calmer place.”
Because sending your credit card details and corporate secrets through the postal system is obviously much safer!
Ref:
mail: http://news.bbc.co.uk/1/hi/northern_ireland/7682004.stm
phone: http://www.bbc.co.uk/news/uk-politics-11820211
Use common sense, if you run a million dollar company from your boat then take care, if you just blog so the family can follow your adventures then you really have nothing to worry about.
A bit like the post – don’t send cash…
PD
Until I set up my own VPN, I had used several, If they created excess overhead or were throttling, I never saw it on WIFI–broadband, yes, but not WIFI.
I found that contention ratio, access point saturation, and people using boosters near the access point to be far more of a problem. On broadband, I saw speeds within a VPN drop to 750Kbs at times. I’ve never seen even a speed fluctuation when comparing WIFI with WIFI+VPN. The WIFI speeds are usually so low changes are lost in “gauge” round off error.
I used the same speed tester inside and outside the VPN. (I also think ISPs give speed test sites preferential treatment).
Jeff Siegel: “But there’s something new that just changed and a lot of people think it changes everything.”
But nothing has changed. And your solution (using WPA) changes nothing either.
Nothing has changed because Firesheep only allows you to momentarily use someone’s else Facebook or Twitter account, certainly not to sniff out passwords. It’s not the end of the world. It is likely that the vulnerability will be fixed.
Your solution changes nothing because WPA with shared key (the mechanism that would be used in marinas) can be cracked in minutes. And the first thing I do when on a network is to break into the router. WPA certainly doesn’t stop me.
Oh, I know what you’ll answer: only uber-leet hackers can do that, not the script-kiddies. But this was precisely the situation just before Firesheep. In other words, the solution you advocate is only good as long as nobody releases a program that makes it useless, which can happen anytime (maybe I’ll do it).
This is really not a big deal. This is part of the same old cat and mouse game. Solutions will appear naturally, regardless of the crusade you’re waging.
And I maintain that the original article is incredibly misleading. The password sniffing near the end has nothing to do with Firesheep, and would have only been relevant to network security maybe 15 years ago.
> But nothing has changed. And your solution (using WPA) changes
> nothing either.
Meanwhile some of the most experienced and respected networking experts suggest otherwise and recommend WPA and the exact things that we recommended on our newsletter. These are experts that have a long track record of providing accurate suggestions.
Instead, the mass of boaters should ignore this and follow the advice of an anonymous source who suggests that sticking ones head in the sand to ignore the threats is the best course of action?
I don’t think so.
Jeff Siegel thinks I am suggesting “sticking ones head in the sand to ignore the threats is the best course of action”.
This is a straw man argument. I am not suggesting such a thing.
In fact I didn’t suggest any particular course of action. I expressed my opinion that the original message and many others that followed were misleading.
I also stated that WPA wasn’t the solution to this problem. In general, believing that you’re safe because a small segment of the communication chain is encrypted is a mistake. (This has been pointed out by others.)
I did read Steve Gibson blog. Two things came up just from skimming the comments:
– From Gibson himself, “there certainly is bad stuff that an attacker can do on a WPA encrypted hotspot when the passphrase is known to all.” (Which, of course, would be the case in marinas and other public spaces.)
– Firesheep has already been used with WPA:
http://allthingstazz.squarespace.com/new-in-technology/
So, I’m not sure who has his head in the sand.
Threats abound. I am always shocked when I see cruisers in the Caribbean or elsewhere do their online banking in cyber cafes. This is much more dangerous than an open WiFi. Not only the staff have access to everything that goes through the network, they also have access to the machines themselves. Keyloggers will record login names, passwords, account numbers, cc numbers, etc., and no amount of encryption will help.
When vulnerabilities on DNS or router protocols come up, nobody except experts talk about them. So why the hubbub with Firesheep, even though the other vulnerabilities are much more dangerous? A couple of things, I think:
1- DNS and routers are harder to understand. Few people know what DNS is, for example.
2- Their vulnerabilities are harder to demonstrate.
Firesheep, on the other hand:
1- is easy to explain. “Evil hackers can hijack your Facebook account!”. Add a few more !!! and mix in a few password sniffing fnords (look up “fnord”) and “it’s the end of the world” (or, like Steve Gibson, “the world was changed forever”), and you’re in business.
2- is easy and spectacular to demo. In other words, what a show!
There is also a positive feedback loop (as you demonstrate), since security experts have an incentive to talk about it and to have an opinion (no matter how unoriginal), which in itself fuels the panic and makes more experts talk about it.
So, what should be done about this particular vulnerability? Twitter and Facebook should fix their sites, which means using https for sensitive information (which in the long term is everything, IMO). People should educate themselves. They should pay attention to what they’re doing and always assume someone is out to get them. They should use ssl (i.e. https, pops, imaps, ssh, etc.).
Tunnels are great, but it should be noted that the protection ends at the end of the tunnel.
As a clarification, WPA doesn’t hurt. It is not the solution, and I think it is misleading and dangerous to imply that it is, but it helps a little nonetheless.
I have much more to say about this. But the point is: there is no silver bullet.
Cheers.
Generate fear and you generate discussion. Discussion is not a bad thing. But generate the fear and then add some smoke and mirrors to try and prove the point and to try and make oneself an “expert” to anyone less educated on the subject, is a common practice on the internet. It is amazing the wealth of accurate information posted here by those considerably more knowledgeable. Sometimes these “life as we know it is over” reports begin almost as a one man campaign to shout, “look how I am trying to save you all.” Everyone would be better served with an accurate and unbiased assessment of the issues of WiFi in general and the tools available to protect yourself, rather than once again the sky is falling. I have directed many discussion located elsewhere on the net to this comment section so that others might benefit from this knowledge and a more informed discussion. Thanks to those that have brought some reason to the table.
I just painfully went through the comments to see if anyone really disagreed about the use of WPA being a wise thing to do….they didn’t. Nobody. The disagreement had to do with the degree of importance WPA had in relation to this discussion of Firesheep type tools. I find some of the comments condescending. Clearly, not all of us share the same definition of “expert.”
So my personal opinion (and it is JUST an opinion): If someone thinks Firesheep is a game changer, then they are not familiar with the game. The only way you could consider this a game changer is if you assume there is a demographic out there that has enough interest and expertise to even run Firesheep that ALSO can’t use a command line interface. You are in more danger of a Script Kiddie setting up the Marina Access Point, which obviously the WPA won’t help. There are a gaggle of easy to use scripts that do evil things all over the internet and we are getting worked up because someone wrote a packet sniffer / parser and made it a browser plug-in? Seriously?
And it’s been trivial for a 14 yr old to do this for a long time – it’s just in a more colorful display now. Maybe that’s why the journalists are so excited. I would argue that any potential game change is because those journalists now just made a big deal of it….so now everyone wants to try it out. In short, they just did all of the marketing and advertising.
On the positive side, perhaps the attention brought by these journalist will have readers getting a bit more educated about the potential vulnerabilities. What is bugging me is that some seem to be implying that WPA is some sort of panacea without also emphasizing the total picture (i.e. beyond the marina).
Here is our approach to WiFi and has been for a while. I would like to hear some comments. We have our disk encrypted on the laptop using Truecrypt. We have a firewall always active and a Virus protection. We also use Malwarebytes and Super Anti-Spyware. Our virus protection has a safe surfing program. We use a VPN called WiTopia and our email programs are Yahoo and Hotmail using their safest settings. So for the average WiFi cruiser using open WiFi when available and Marina or Hotel Wifi often, What else can the average cruiser do to protect themselves and how vulnerable am I really?
tursiops wrote:
> The only way you could consider this a game changer is if
> you assume there is a demographic out there that has enough
> interest and expertise to even run Firesheep that ALSO can’t
> use a command line interface.
That’s part of it. Although cracking some things takes a lot more than a command line. And that’s the whole point. The enormous exposure of Firesheep has spawned a variety of new tools that process a lot of data to help make hacking easy. There have been multiple new tools released. There will be many more.
Chuck wrote:
> and how vulnerable am I really?
I think you’re the most vulnerable type of person out there because you think you’re doing everything you should but deep down, you really don’t understand the underlying technologies or how they work. Your comments here are doing a disservice to all cruisers.
The fact that you’ve started using WiTopia tells me that you do believe there is a threat to the average boater who doesn’t use VPN technology. You were smart to follow my advice. You shouldn’t be discrediting my advice to the others who need to hear it.
I’ll make an incredibly ballsy challenge to you. You know me and you surely wouldn’t allow me to obtain any of your private information, right? Give me 48 hours to hack into your personal accounts. Promise me that you’ll stop using WiTopia for that 48 hour period starting immediately. I promise to not do any damage and you promise to hold me harmless for any violation of security that I perform. I’ll generate some proof of the hacking and you have to leave it for another 48 hours so everyone here can see it. I’ll leave WaterwayGuide.com alone and just go after personal info.
Deal?
My goal is to once and for all demonstrate how vulnerable most people are. This is an important issue and you shouldn’t turn it into something personal.
Jeff you obviously know how to exploit security flaws with the internet, but you realize the person you are asking permission to hack or gain access to his personal information is against federal law? He can not give you permission that could keep you out of legal hot water? It’s called theft of service and identity theft. Here is an example, when I was in law enforcement you just purchased a new Ferrari and want to open her up I tell you it’s “ok” for you to do 140mph down the highway, you do but another trooper from a different jurisdiction gets you on radar you tell him officer Bill gave you permission guess what you would get a ticket and face the consequences. What you are advocating doing is against the law and cyber crimes are taken seriously. Your not good enough to not get caught either especially after you post about it in a public forum. Unless you are on the same WiFi AP your simply proving other’s points that a WPA enabled Hotspot is only one part of the path to one’s passwords and personal information on the super highway called the internet.
Bill Lentz
Blimey Jeff, that’s a bit drastic…
Steve
Huh Jeff, what exactly are you proving by that. If Chuck does not use his VPN on an open network, he will be vulnerable; we all agree on that.
The upshot of all of this sky is falling talk is that access points that used to open (and safe to those using VPN) will now be closed and boaters will have fewer options for getting onto the internet.
The “average boater” is perfectly capable of using commercial VPN solutions, you should encourage that rather than discouraging the use of wifi on open networks.
Steve
First of all there is no way I will give anyone permission to hack into my personal information, and are you asking me to give you permission to break the law? I have not just begun to use WiTopia, we have used it for quite some time and so far I am satisfied. No one said there are no issues with WiFi or wired internet nor is anyone saying that the average person should not take security precautions. But some of these posts such as this last is quite over the top and I will let others take from it what they will. I just want to verify that you want to go after my personal info but you will leave a business site that I work for alone. Why would you want to go after MY personal information and not the others here that disagree with you? What does any of that have to do with the discussion that has been taking place here. And I certainly would like to hear from others as to my previous questions.
Chuck, FWIW the only thing I would do with your setup, is to change from AntimalwareBytes, to a combination of the IoBit ASC (advanced systems pro) and IoBIT security 360. When I made the change some months ago it found dozens of things that AniMalware and the dreaded Norton and Macafee hadnt picked up at all. New definitions to 360 Pro come down daily almost sometimes twice a day, so it’s really on the ball.
Ive got rid of the A/V S/W and antimalware and PC tools and now just rely solely on these.
ASC even stopped me from opening an Email it deemed suspicious.
Just My opinion and small experience.
Steve
Jeff said: “That’s part of it. Although cracking some things takes a lot more than a command line. And that’s the whole point. The enormous exposure of Firesheep has spawned a variety of new tools that process a lot of data to help make hacking easy. There have been multiple new tools released. There will be many more.”
*Sigh* Why did I know that would be the response.
Thanks Steverow, I will take a serious look at your suggestions. Chuck
Chuck wrote: “What else can the average cruiser do to protect themselves and how vulnerable am I really?”
Chuck….just my opinion….your system sounds reasonable to me in the sense that it will keep out most people except those specifically targeting you (which may or may not be personal). You haven’t made it trivial to break in, so like locking your door, most evil doers will just move on to an easier target. But I can add some of my thoughts just because you asked for more opinions….some of these will take some effort.
1. I think Chris’ post (11/19) did a pretty good job of spelling basic precautions out so no need to repeat those recommendations. Although, it was long so I apologize if I repeat a few things.
2. You didn’t mention if it is a hardware or software fireware. I use both, but even more importantly is the correct set up. Close ports you don’t use. There are several other precautions to take that get progressively more complicated…..this could be it’s own thread. Good firewalls can get complicated quickly. Some vendors offer a service to help you set it up based on what you want to do.
3. Make sure you are using your operating system correctly with regards to accounts. Don’t use an account that has administrator (or root) access. Create a separate account for your daily business that can’t access you system files.
4. Limit your time on the network. Reading and composing emails doesn’t require a connection, so why be connected until ready to send/receive?
5. Find a password protection system that generates really strong passwords and stores them encrypted on your system. Rotate often. A master password or phrase will allow you a way to change these, so store the master password somewhere else – multiple places since loosing it will really mess you up 🙂 I have mine on a few separate usb drives.
That will take care of most invaders, but as you can see, security is as much about being prudent with your operating habits as it is with the hardware/software installed. Most break-ins are social engineering, default passwords, etc.
I think most of what I suggested is reasonable for the average cruiser to do/learn. You can take this much further, but it reaches a point of diminishing returns since you still want your system to be useful and probably aren’t looking for another occupation in network security. If I really want my system hack-proof, I would turn it off and fill it full of concrete…but I’m not entirely sure about that either 😉
Hope that helped some….
Reprinted from comments at this thread:
Now, the “never use open wifi” basically then means “use at your own peril” if you have no other choice. But the website she points to is really an excellent and easy step-by-step to secure your online experience.
tursiops, This is exactly the type of information that needs to be discussed and relayed to the average cruiser that has either only Wifi for online use or Wifi as a supplemental to aircards and other connection methods while under way. It is also information that is usable and easily understood for the average cruiser. I consider myself an average cruiser. As Jeff Siegel pointed out, I am not an expert on the underlying technology, nor do I want to be. And I believe most cruisers also fall into this category. I am an individual knowledgeable in boating systems and I have kept up with the latest technology as best I can for the purpose of making a living in the marine industry. I consider my self knowledgeable, but by no means an expert. I have been boating and cruising for decades and have watched closely as technology has changed. I am by no means a techy that went out and bought a boat and made a trip or two down the ICW and am now an expert in all things technical and boating. I come to sites like this to learn from folks that have the information that I lack. I don’t need to know how the internet works, I need to know what the vulnerabilities are, in a calm and rational fashion, and what steps I need to take to reasonably protect myself within my realm of knowledge. I believe that if most boaters weigh in on the subject they would agree. I think that is what much of this discussion is about. Many folks have emailed me and were thoroughly confused by all of these “alerts” posted all over the internet. It is discussions like this that are easing some of those fears and at the same time giving folks an honest and working understanding of these vulnerabilities without encasing your computer in concrete as was mentioned. Many emails I received were “my god, what do I do now.” In every case I have directed them here and the replies have been very positive. Thanks to everyone, I have come away with new understanding to add to my arsenal.
Theoretical vs practical threats…
When I was 14, I was a hacker. Back some 38 years ago we didn’t have that name. We were just a group of geeky teenagers who liked to push computer operating systems to their limits and gain access to things we weren’t allowed to see. I learned more about software in those years than through any of the degrees in Computer Science I’ve earned since. There was an elegance and creativity to finding solutions that no normal software development could match. It was very cool.
I’ve stayed involved with the black arts since then. As an old man in this field, I’ve tried to counsel some new rising hackers to show them how their talents could be used in more lucrative ways. That rarely works until they’re a little older and care more about money, cars, and girls.
So with this background, I heard about Eric Butler’s Firesheep announcement on October 24th. It’s odd to have a hacker announcement like that – even odder to provide the source to the code so openly. By the 25th I was looking at Eric’s code. It was different. Instead of being very obtuse and difficult to understand, it was written as if a pro had crafted it. It had an easy-to-use interface that anyone could use to process the network traffic through an existing tool called WinPcap. Also on the 25th, ABC News picked up the story. Now this was really different. The media attention was major.
On the hacker forums, trust me, this was noticed. All of a sudden, all of the 14 year olds out there wanted to be Eric Butler. Some started discussing other user-friendly tools that they could write – things much more dangerous to normal users than grabbing their Facebook account for a session. Each new article, blog posting, and news story about Firesheep fanned what should have been a smoldering flame. It turned it into a roaring fire.
Over the next three full weeks this continued. It continues today. But the conversations now were about testing these new tools on open networks. I was seeing more and more open testing and experimentation on normal unsuspecting users, the bulk of WiFi users out there, especially cruising boaters. After 23 days of this, I wrote the section in our newsletter warning our users to stop using open WiFi routers. It wasn’t “the sky is falling” type of outcry. It was quite simple because a complex message would get lost. Many of our users look to us for this type of technical, internet advice and I felt it was my responsibility to convey what I knew. It was at that point that some theoretical threats became practical and many more people were open to attack.
Immediately a few people who know a fair amount about networking pointed out how these theoretical threats have always existed. My suggested WPA short-term solution could be hacked too. And in fact, WPA isn’t a perfect solution. To show what I mean, check out these instructions for cracking a WPA encrypted stream:
http://www.aircrack-ng.org/doku.php?id=cracking_wpa
Please read that and see how impossible it is to follow – and that’s one of the better sets of cracking instructions. It’s the type of thing that can be accomplished by very few people – even with step-by-step instructions like that. So does WPA make you safe? No way. But it’s an easy first line of defense for now. It’s sort of like a padlock. It can be broken with the right tool but it stops 99% of would-be threats. Of course once an easy-to-use WPA crack tool comes out, WPA will be worthless. I give that a few months to happen.
Getting full network protection requires something stronger. The gold standard is VPN technology. That’s like an armed guard next to your padlock. The only issue is that you have to make sure the guard won’t be the one stealing from you when you leave. VPN technology transfers trust to the provider, much like having that armed guard.
I really tried to make this theoretical vs practical argument here over the last week. The major points I’ve tried to make seem to have gotten lost by some. Others are interested in personally attacking me for reasons that have nothing to do with WiFi, threats, or anything pertinent to the discussion.
I had hoped to demonstrate some hacking techniques mainly to stop the personal attack and show that I had some experience with all of this. As an aside, legal experts are in disagreement about the criminal aspects of grabbing network traffic on an open, unlocked network. If you’re on an open network and manually ask to be connected to it knowing it is unlocked, there should be little expectation that you have a private channel of communication. This has yet to be tested in court and many hackers know this. It’s yet another threat because many see this as freedom to snoop on open WiFi.
I’ve said more than enough about this although I’m happy to answer questions. I’ll definitely continue to warn our users in a calm and direct way along with providing them solutions to the threats. Others might try to confuse the message, but ultimately, we’re trusted by our users and they listen to us. It’s one of the best things about this little ActiveCaptain project of ours.
So Jeff when will Active Captain be selling a VPN solution for cruisers? I’m sure I’m not the only one seeing a theme here.
Bill Lentz
> So Jeff when will Active Captain be selling a VPN solution for cruisers?
Not now, not ever.
Perhaps you missed my posting above where I discussed how I’ve been evaluating over a hundred VPN providers to find one appropriate to meet the requirements needed for cruising boaters. Had you seen that, you might not be imagining themes.
Good for you Jeff, I didn’t miss any of your post’s.
Good luck.
Bill Lentz
Jeff-
You are no hacker. I doubt you were ever one. I knew this the moment you tried to make Ben (and us) believe you were doing something cool by sniffing your own passwords on your own machine using unencrypted POP. Other comments on WPA in other forums have convinced me further.
You are worried about people who use Firesheep but not about people who use aircrack because aircrack has too many steps to follow?! Seriously?
I’m sure not worried about people who use Firesheep but are incapable of using aircrack. They are annoying, at most, but not dangerous.
Aircrack isn’t difficult to use. You also seem to forget (here and elsewhere) that most of the steps are irrelevant because the pass-phrase is already known in the case that interests us.
So you’ve read Butler’s code. Good for you. Have you read his own opinion about WPA etc.? Here it goes:
http://codebutler.com/firesheep-a-day-later
…
Things NOT to do (debunking suggestions from other people/sites in response to Firesheep)
Stop using open WiFi
In response to Firesheep, lots of people are quick to say “Don’t use open wifi”. While open wifi is the prime proving ground for Firesheep, it’s not the problem. This isn’t a direct vulnerability in wifi, it’s the lack of security from the sites you’re using. Abundant, free, open wifi is great to have, it can be very useful. Low-risk activities like reading the news, looking up a nearby business or finding a bus route can be done without being logged in to such sites and risking loss of any important sessions, for example.
A password-protected (WPA2) wireless network or even a wired network just requires that attackers perform one more step to carry out this attack. This might be ARP poisoning or DNS spoofing, neither of which are difficult to carry out. Go and download Cain & Abel and try it out on your network, it’s not that much harder than using Firesheep, and it’s been around for nearly a decade. There are other tools that’ve been around longer.
Another problem is that anyone who has your wireless password could set up their own rogue access point. If they have the stronger signal than the “official” access point everyone in the room will automatically connect to it instead and begin sending all their traffic to the attacker. WPA2 Enterprise was designed to solve this problem by allowing clients to verify the authenticity of the access point they are connected to. Unfortunately in addition to being very difficult to configure, a flaw known as “Hole 196” was recently discovered allowing users on the same network to spy on each other.
For these reasons it’s not very helpful to just enable WPA2 and write the password on the wall. Doing so might actually give users a dangerously false sense of security.
[end of quote]
I couldn’t agree more.
Cheers.
Aside from the anonymous personal attack from Ms. Pandora, why would anyone follow the advice of Eric Butler? Instead, I’d look to networking and security experts like Steve Gibson who aren’t worried about their personal liability with Firesheep:
http://steve.grc.com/2010/10/28/why-firesheeps-time-has-come/
Quoting from his posting released 3 days after Firesheep came out:
What needs to change? … Exactly two things:
1. WiFi hotspots must encrypt. Period. They can still remain free and open, but they must use WPA encryption to protect their users from casual eavesdropping…
2. The bigger change that must also be made is for all vendors of web services to switch their connections over to using the SSL/TLS protocol exclusively…
He’s suggesting to not use open WiFi and for sites to switch to SSL support. The only message that the cruising boaters should walk away from with that is: Don’t use open WiFi.
To emphasize the point, Mr. Gibson released another posting that day:
http://steve.grc.com/2010/10/28/instant-hotspot-protection-from-firesheep/
His quote there is:
Amid all the fury over the release of Firesheep, no one else seems to have noticed, or at least mentioned, that the only thing any WiFi hotspot needs to do to protect its users is activate WPA encryption using any simple publicly-known password.
“Protecting its users” is his objective. Staying away from open WiFi is the method.
It’s fascinating to see how many people have downloaded Firesheep. The statistics are here:
https://github.com/codebutler/firesheep/downloads
As of this morning, 855,000 downloads occurred. After looking at the current number, go back 5 minutes later and see how it jumped.
Ms Pandora – expose yourself to show your real motives with these postings. Your anonymous misinformation is an insult to the discussion and this site and I’m done responding to it.
Yeah, I wish people would avoid snide and personal comments. It detracts from the value of this conversation. It also makes me unhappy to read my own blog, and that sucks.
Some of my comments weren’t totally appropriate. I should have refrained from making personal remarks. I love this blog and I don’t want to be the one lowering its value.
I apologize.
For everything else, I stand by what I said. In particular I think Eric Butler’s quote is relevant.
I also think all Firesheep has done is allow incompetent people to become annoying. The upshot is that Facebook and Twitter will have to pay more attention to security.
The real threats are still there. And the proposed solution to protect against Firesheep only will give a false sense of security.
Last, I am not going to give up anonymity. My reasons for this are mine alone. I myself look at credentials with much skepticism. I don’t believe that what people say should be judged based on who said it. Good arguments/ideas are good even when stated by people whose credentials are unknown.
Just me, I guess.
Cheers.
Chuck said: “I don’t need to know how the internet works, I need to know what the vulnerabilities are, in a calm and rational fashion, and what steps I need to take to reasonably protect myself within my realm of knowledge.”
This is a good sentiment and this should be the goal of the discussion.
It’s also nearly impossible. If you sail in a piracy region, you want to know the risks and how to minimize them, but you can’t make them zero. If you sail in a mosquito region, you can use screens, but if there is any tiny hole, the mozzies will find it. They are persistent if not intelligent. If you work for airport security screening, everyone is a potential terrorist, even the little old lady with some knitting. Security is hard,
and it can be very inconvenient to the people who are being protected.
To protect yourself on the internet, you either need to know a lot about how it works or you need to get advice from someone you trust about what not to do.
The list of steps to take begins with how you set up and use your computer/device. Open WiFi networks are just one item in a long list.
And then you have to convince the sites you use that they need to fix their security…
Firesheep downloads are 871k…may hit 1 million by the end of this week.
Has anyone considered – who are these 1 million people downloading it and what will they be doing with it, and WHERE? I think its going to be lots of curious people with laptops in all kinds of public places: airports, restaurants, even entire municipalities have instituted open WiFi networks.
I can imagine college campuses being infiltrated heavily with FIRESHEEP, where FB and other social networks is also commonly used. Watch and see what happens when Firesheep is integrated to Ebay Pay Pal, which is planned. This is far more than a nuisance. Its personal invasion. And as has already been stated, is illegal.
I have been reading about this for several weeks now, including this entire thread. I’ve also listened to numerous Steve Gibson podcasts about it.
Steve Gibson’s blog says
“The ease and simplicity of using Firesheep has transformed web session hijacking from a mysterious command-line driven black art into something for the masses. This is huge.I said above “the world was changed forever” because I can’t see how it could remain the way it has been in the face of point-and-click web session hijacking.”
My conclusion is FIRESHEEP is here today. Its relatively easy to foil it once you understand it.
Yes web side needs to change their process and start using SSL. Gmail has already done it and Hotmail just included this option this week. But we all know that the web side solution will be slow in coming.
I’m staying off of open WiFi networks in the meantime….and probably for a long time in the future as well.
Ben thanks for the article !
R.
There is an OS X equivolent of Firesheep called KisMac.
http://trac.kismac-ng.org/
The chipset on Macbooks currently does not support packet injection, but there are plenty of USB-based Wifi devices that are supported.
KisMac also does sniffing, which of course is the most dangerous of features offered by software of this kind.
Be careful out there and make sure to use the latest and great of crypto protocols for your floating network.
Yes, Thank You Ben, and thank you fellow readers.
This continues to be an invaluable blog and follow-up discussion.
Thanks to Steve and Chuck for the heads up on Witopia.
I switched from the free HotspotShield to Witopia, it’s really easy to set up on multiple machines (but you can only use one at a time). I got the $59 annual package which allows access to a long list of US and international VPN gateways. I don’t notice any slow down and on some video streaming sites I even see faster throughput.
Recommended.
Derek
The good John Harries also chose Witopia and has a good write up on installing it:
http://www.morganscloud.com/2010/12/04/safe-wifi-access/
WiTopia is OK – they’re in my top 3. But right now I think there’s a better one for less money, better support, and better software for OpenVPN connections when you need that (Windows/Mac use to provide better performance). I’m trying to do some performance testing – really difficult from Bald Head Island on a weekend…
Maybe it’s me but I also love the idea of being able to capture streamed video for playback later. I find that we like to record programs so we don’t have to watch them live when you have a slower connection – common on a boat. There’s a VPN that provides that type of stream video capture along with their product. If I have to pay for security, I’ll do it. It’s just nice getting something else along for the price.
One thing that is hidden about many VPN’s is that they block VOIP and applications like Skype and other P2P clients. That’s really unfortunate when on a boat – sometimes you just have to be able to use Skype or do screen sharing/presentations on a remote screen. WiTopia allows Skype but they’re unclear about other P2P/Torrent connections in terms of allowing them or throttling them.
There are many issues.
I’d looked at WiTopia, but although they have a lot of US servers, not too many in Europe. In the UK only London and Manchester both a fair distance from the Midlands where I live or most of the coasts that cruisers will use. I don’t know of one that has lots of European portals any one else know?
Skype and similar programs are a BIG issue and so is BT/P-P client usage, as is video streaming If I want to watch US or CAN TV and you want to watch the BBC/ITV/CH4/CH5 or SKY et al. The speed concerns me too, because of the amount of extra overhead in encryption and transport, but that said I can watch BBC iPlayer satisfactorily on a HSPA link, most places in the UK..at about 3.6Mbps or better at 7.2Mbps if the cell site is uncapped. Some Voda ones are now 14.4.
Steve
I bought Air Crack at a Computer Show yesterday. The vendor had sold several dozen copies to people too lazy to download it. Its easier to learn than Face Book. I’ve since logged on to every WPA2 network I can see.
So; if not VPN, what is there when you need to pay a bill in the islands?
First VPN protects you as long as you can trust the VPN. A VPN will protect you on a completely open network connection too.
Air Crack is great for obtaining the WPA passcode. That’s still far from being able to decode everyone else’s network traffic – that’s why a WPA/WPA2 locked router is the short-term fix to protect yourself. The advantage of using WPA/WPA2 is that it uses the passcode to create a different encryption key for every user. I’m not saying it’s impossible to crack that too but the tools to do it are more difficult.
For now.
Today we published our final VPN analysis including recommendations for 2 different services. We further negotiated a 40% discount for each service for boating use. Read it all at:
https://www.activecaptain.com/newsletters/2011-01-05.php